What appeared at first to be a VPN backup database leak has now allegedly turned into a full-blown website breach. According to the hacker behind the leak, they have taken down LimeVPN’s website, and with it, the website’s server. The hacker alleges to have the entire contents of LimeVPN’s website server, which consists of sensitive account information including usernames, passwords, and payment details and is selling these to the highest bidder. PrivacySharks has spoken with LimeVPN and the hacker behind the attack, who claims to be in possession of this data, to gather more information about the leak.
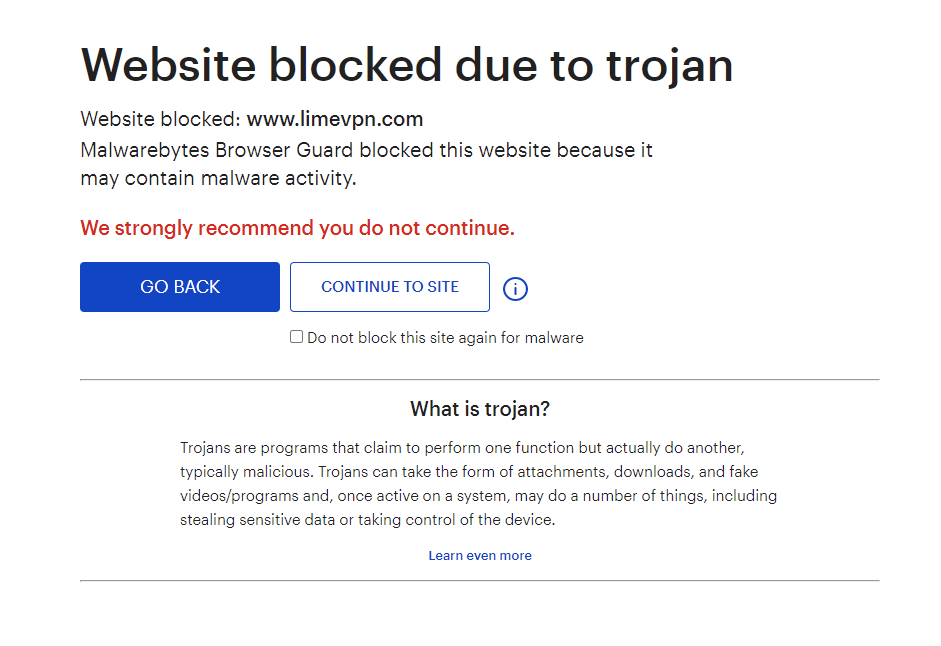
Update #3 05/07-2021: LimeVPN has released a (poorly written) statement on the situation. The company states that no credit card details were a part of the leak and estimates that 800+ users have been affected (which means that thousands of users could still have been affected.) However, LimeVPN doesn’t believe that users need to be concerned about the leak. (Read: They’re still not sure exactly what was leaked – disturbing) Despite countless emails to LimeVPN asking for a statement and concrete evidence to counteract the claims made by the hacker, we have still heard nothing from them. Using the Malwarebytes Browser Guard the LimeVPN website is still blocked due to trojan. We do not recommend you try to enter their website.
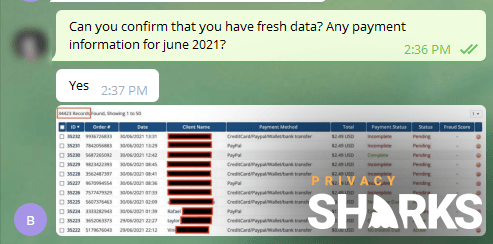
Update #2 01/07-2021: We have spoken with the hacker selling the original database, and they allege that they have taken down the VPN provider, LimeVPN’s, website. They are now selling the entire website backup at a much higher price. They also claim to have a fresh database with thousands of customer data records, including emails, passwords, IP addresses, and payment information.
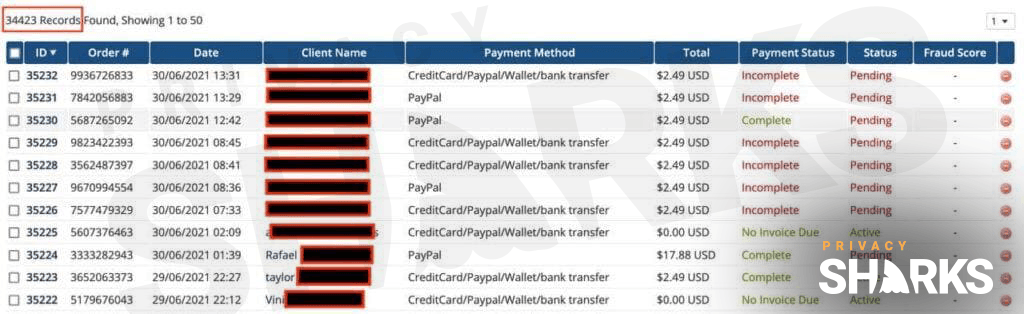
Update #1 01/07-2021: Shortly after contacting LimeVPN (to confirm the breach on their backup server) and revealing the leak to them, their website went down. Worryingly, our access was blocked by Malwarebytes due to a potential Trojan found on the site. Looking at the leaked files, there are payment confirmations from customers in June 2021.
Website still affected by Trojan – Screenshot taken 05/07-2021 1:20PM CET
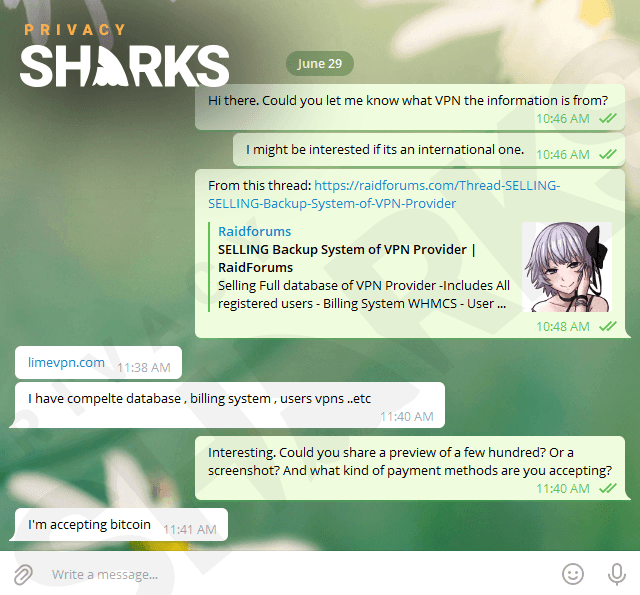
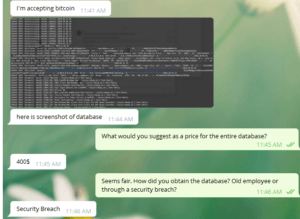
LimeVPN, a supposed no-logs VPN service, has found itself in the midst of a massive data breach that puts thousands of users at risk. A user, known as slashx, posted on popular hacker forum RaidForums on 29th June 2021, advertising LimeVPN’s entire database for sale. We contacted the seller immediately to learn more about the breach.
What does the leak include?
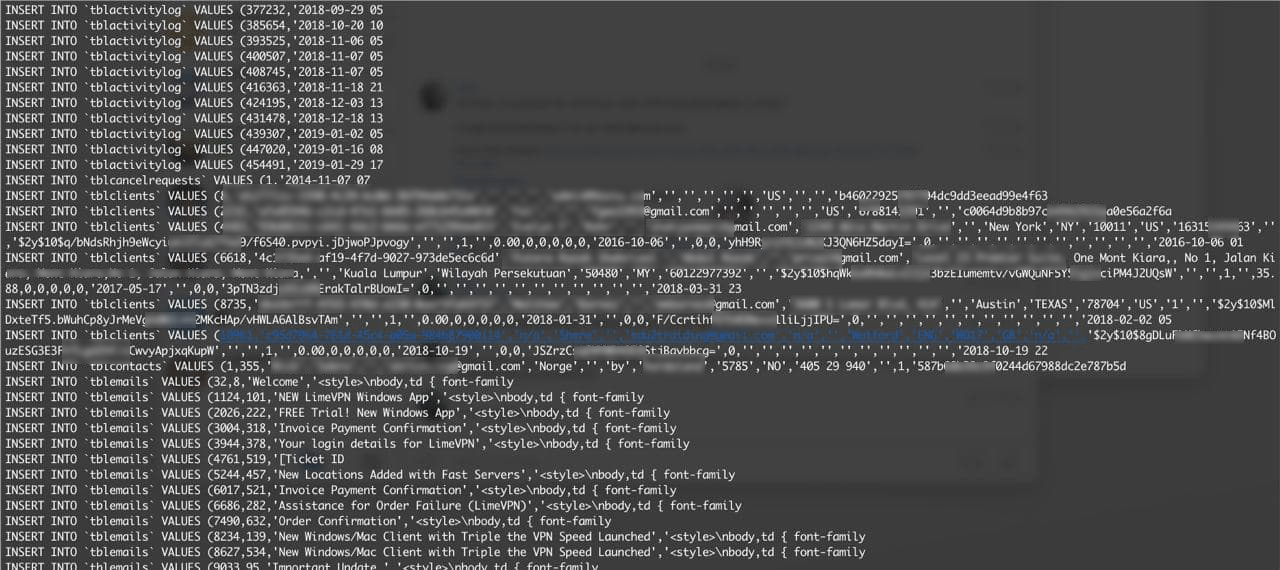
Our security team has been in direct contact with the hacker and can reveal that the scraped data includes everything from LimeVPN’s database. This includes:
- Records from its WHMCS billing system.
- VPN account details like usernames, email addresses, and passwords.
In a conversation with a member of our team, the hacker revealed that they got their hands on LimeVPN’s data via a security breach and not through an old employee. The individual behind the breach is currently asking for a $400 Bitcoin payment for the entire contents of the database, which they say affects just over 10,000 users.
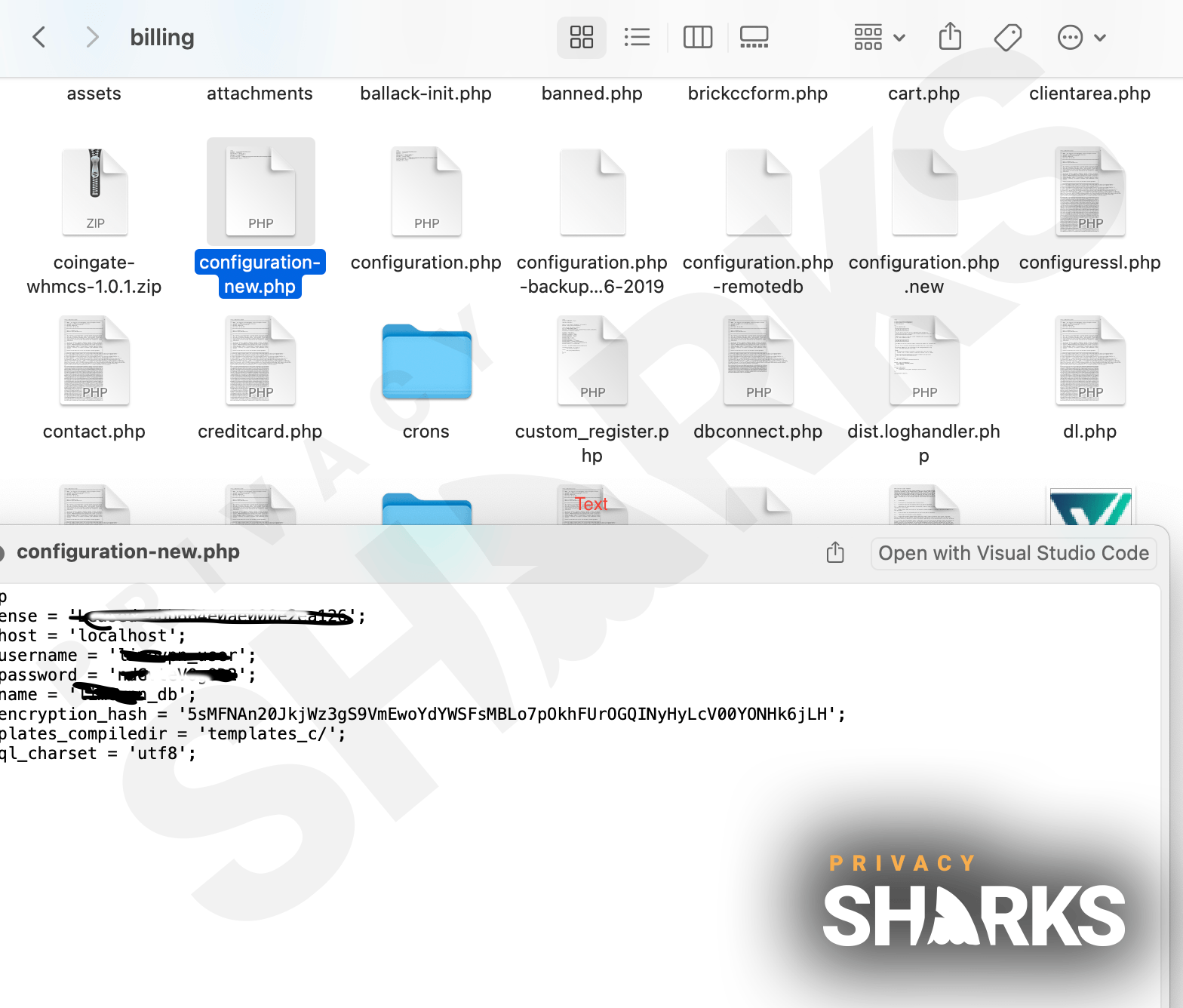
We have also seen a screenshot of the leaked database and can confirm that it does include the sensitive information listed above. As well as this, the hacker informed us that they have the private keys of every user, which is a serious security issue as it means they can easily decrypt every LimeVPN user’s traffic.
What does the breach mean for LimeVPN?
VPN providers make their money reassuring users that their data will be private and secure with them. The fact that LimeVPN has had its entire database scraped in a security breach is a severe blow to the company’s image. It will undoubtedly have a damaging effect on its reputation with internet users.
LimeVPN’s no-logs policy will also be thrown into question since this massive data breach may lead some users to question how much of their data the company actually stores. Without an independent audit of the provider’s privacy policy, the phrase ‘no-logs’ doesn’t have much weight, and the current situation will cause a lot of skepticism from customers.
We reached out to LimeVPN for comment. However, after endless attempts to get in touch with the press team, the only response we received from a customer support representative was a disappointing “I am checking with the concerned person for this.”
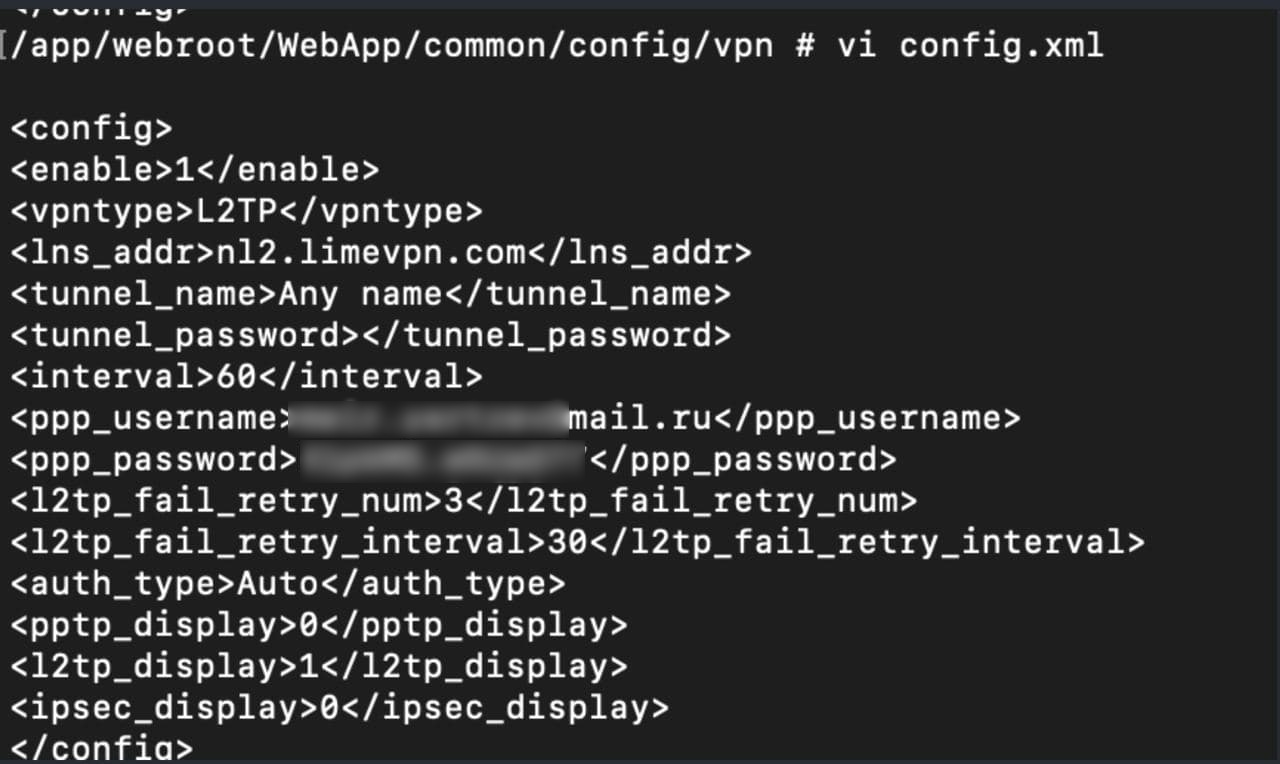
I’m a LimeVPN user – what should I do?
If you’re a LimeVPN user and fear that you’ve been affected by this breach, we advise that you reach out to the LimeVPN customer support team for verification (Update: We no longer recommend you contact the team. Instead, change your passwords and order a new credit card). If you have been, then it is worth asking the company if they are offering any compensation to users affected by the breach.
You can also visit Have I Been Pwned to see if your email address or phone number is linked to this or any other data breach.
As well as the above, we recommend immediately changing your LimeVPN account password and any passwords linked to the account used for payment. It’s also a good idea to activate two-factor authentication on your bank account and change your security questions.
Hackers can take information to build profiles on individuals, making it easier to find out more details, leading to identity theft, fraud, or scams. For this reason, it is important to be vigilant when creating online accounts with your personal details. Make sure that you don’t reuse passwords, as this makes it easier for hackers to access multiple accounts. We recommend employing a password manager to help you create strong passwords and using burner email addresses when possible to avoid experiencing the consequences of breaches like this.
Additional proof of breach:

Hi, I'm Cliff. I'm based in Cleveland, Ohio, with my wife and two kids.
I have a keen interest in cybersecurity and have been writing about it for around a decade now. Due to my background in computer science, I am familiar ...
Read more about the author




